Best way to store encryption keys in java images are available in this site. Best way to store encryption keys in java are a topic that is being searched for and liked by netizens today. You can Download the Best way to store encryption keys in java files here. Download all free images.
If you’re searching for best way to store encryption keys in java images information related to the best way to store encryption keys in java interest, you have visit the right blog. Our site frequently gives you hints for seeing the highest quality video and picture content, please kindly search and locate more informative video articles and graphics that fit your interests.
Ask Sawal is a question answer discussion forum. Create a KeyStore object The getInstance method of the KeyStore class of the javasecurity package accepts a string value representing the type of the keystore and returns a KeyStore object. 07122018 How to Securely Store a Password in Java java security encryption hashing. To store a key in the keystore follow the steps given below. We have keys generated every few days and when decrypting we have to try all our keys because we do not know which day the encryption took place.
Best Way To Store Encryption Keys In Java. Hashing is 1-way encryption is 2-way. Symmetric key encryption means that the same cryptographic key is used to encrypt and. What we did was to encrypt the keys one more time and store them as secretes. I have a java properties object with authentication information for a web service.
 Commvault Management Of Encryption Keys From documentation.commvault.com
Commvault Management Of Encryption Keys From documentation.commvault.com
You have got a number of options with storing the key in a HSM being the most secure. The decryption key is related to the encryption key but is not always identical to it. Fundamentally there are two types of keyscryptosystems based on the type of encryption-decryption algorithms. What are the best practices around encrypting this data and retrieving it in a secure way. We have keys generated every few days and when decrypting we have to try all our keys because we do not know which day the encryption took place. This protects against offline attacks unless they capture the key out of RAM which is tougher to do.
How does one correctly create and access a KeyStore in java to store an encryption key.
07122018 How to Securely Store a Password in Java java security encryption hashing. What are the best practices around encrypting this data and retrieving it in a secure way. The decryption key is related to the encryption key but is not always identical to it. I need to encrypt that data but I dont know where I need to store the encryption key for it to remain secure. In other words you cant decrypt a hash you can only check that rehashing the same value. 06042009 We have a slightly different but related issue.
 Source: stackoverflow.com
Source: stackoverflow.com
Similar to the option above but also different. Fundamentally there are two types of keyscryptosystems based on the type of encryption-decryption algorithms. Type in the encryption key when you start up store it in memory. 06042009 We have a slightly different but related issue. 08122011 I have a java properties object with authentication information for a web service.
 Source: thesslstore.com
Source: thesslstore.com
Here you can find answers for more than 5 Million questions. The receiver inputs the decryption key into the decryption algorithm along with the cipher text in order to compute the plaintext. What we did was to encrypt the keys one more time and store them as secretes. This protects against offline attacks unless they capture the key out of RAM which is tougher to do. If your platform offers any kind of protected storage you may want to use that.
 Source: docs.mongodb.com
Source: docs.mongodb.com
I need to encrypt that data but I dont know where I need to store the encryption key for it to remain secure. I need to encrypt that data but I dont know where I need to store the encryption key for it to remain secure. Whats the best method to use store encryption keys in MySQL. Check this Answer for the question Whats the best method to use store encryption keys in mysql in PHP Server Side Scripting Language. I need to encrypt that data but I dont know where I need to store the encryption key for it to remain secure.
 Source: keyfactor.com
Source: keyfactor.com
Mathematically half of them are EVEN DUMBER. Else you can store it in a key store or even a Key encryption Key KEK option can be used. Hashing is 1-way encryption is 2-way. Ask Sawal is a question answer discussion forum. Fundamentally there are two types of keyscryptosystems based on the type of encryption-decryption algorithms.
![]() Source: thesslstore.com
Source: thesslstore.com
This protects against offline attacks unless they capture the key out of RAM which is tougher to do. What are the best practices around encrypting this data and retrieving it in a secure way. In other words you cant decrypt a hash you can only check that rehashing the same value. What we did was to encrypt the keys one more time and store them as secretes. I need to encrypt that data but I dont know where I need to store the encryption key for it to remain secure.
 Source: cloud.google.com
Source: cloud.google.com
06042009 We have a slightly different but related issue. This protects against offline attacks unless they capture the key out of RAM which is tougher to do. What are the best practices around encrypting this data and retrieving it in a secure way. 08122011 I have a java properties object with authentication information for a web service. Ask Sawal is a question answer discussion forum.
 Source: pinterest.com
Source: pinterest.com
This protects against offline attacks unless they capture the key out of RAM which is tougher to do. We have keys generated every few days and when decrypting we have to try all our keys because we do not know which day the encryption took place. However the server boots into an unusuable state requiring you to manually supply the key before work can be done. Whats the best method to use store encryption keys in MySQL. This protects against offline attacks unless they capture the key out of RAM which is tougher to do.
 Source: thesslstore.com
Source: thesslstore.com
We have keys generated every few days and when decrypting we have to try all our keys because we do not know which day the encryption took place. What are the best practices around encrypting this data and retrieving it in a secure way. This protects against offline attacks unless they capture the key out of RAM which is tougher to do. I need to encrypt that data but I dont know where I need to store the encryption key for it to remain secure. In other words you cant decrypt a hash you can only check that rehashing the same value.
 Source: cloud.google.com
Source: cloud.google.com
08122011 I have a java properties object with authentication information for a web service. As for the encryption key thats a much harder issue - definitely dont store it in the database. Type in the encryption key when you start up store it in memory. Whats the best method to use store encryption keys in MySQL. Check this Answer for the question Whats the best method to use store encryption keys in mysql in PHP Server Side Scripting Language.
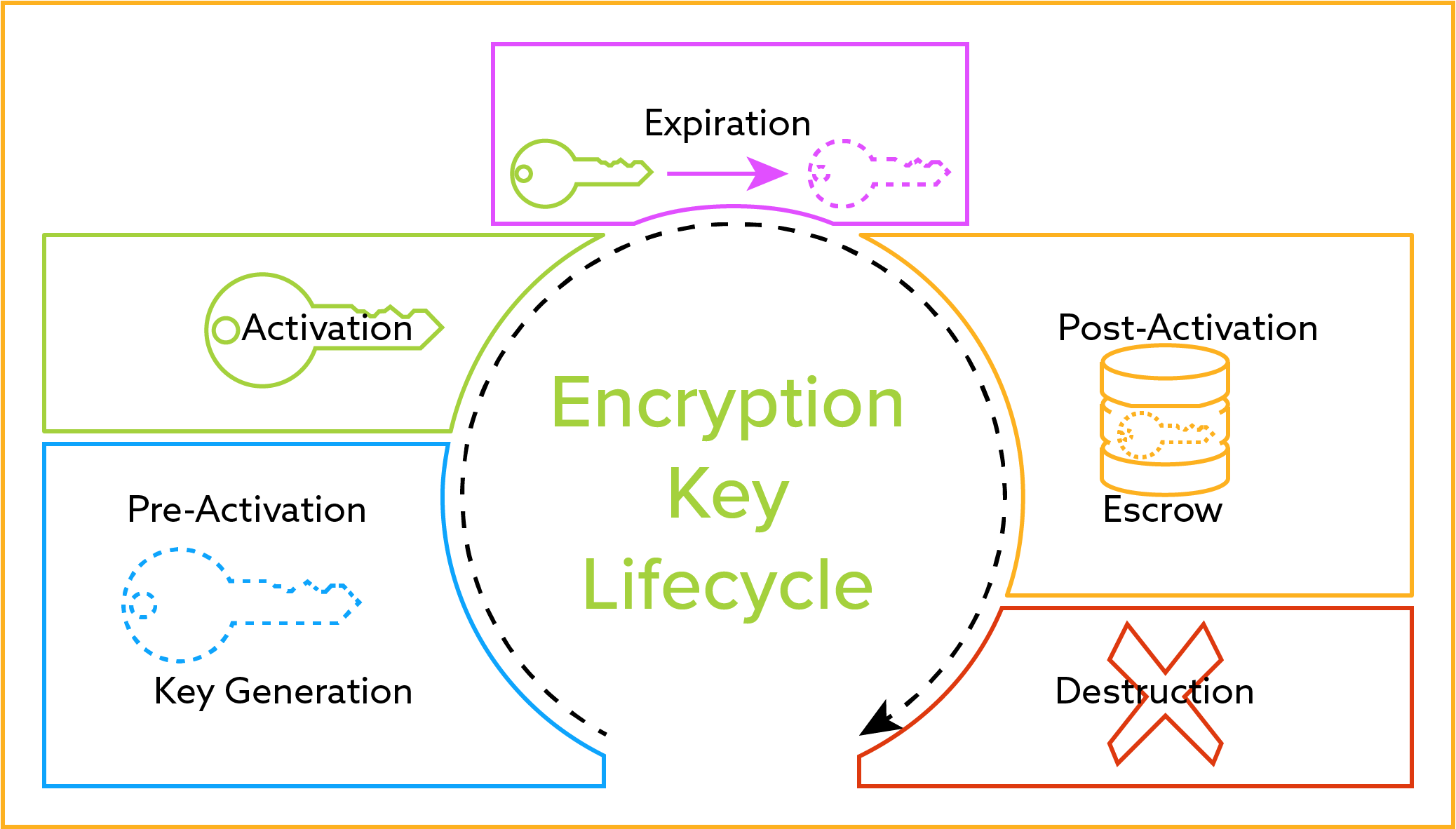 Source: info.townsendsecurity.com
Source: info.townsendsecurity.com
What are the best practices around encrypting this data and retrieving it in a secure way. What are the best practices around encrypting this data and retrieving it in a secure way. What are the best practices around encrypting this data and retrieving it in a secure way. Similar to the option above but also different. Is there any advantage to using a keystore.
 Source: cloud.google.com
Source: cloud.google.com
Similar to the option above but also different. Here you can find answers for more than 5 Million questions. Similar to the option above but also different. If your platform offers any kind of protected storage you may want to use that. Type in the encryption key when you start up store it in memory.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title best way to store encryption keys in java by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






